A critical vulnerability, CVE-2025-5182, has been disclosed, impacting web applications that rely on popular frameworks like React.js and Next.js. This vulnerability is rated 10 out of 10 (the worse), the flaw allows unauthenticated remote code execution through insecure deserialization in React Server Components and the Next.js App Router. Exploitation requires nothing more than a crafted HTTP request, making it alarmingly simple for attackers to compromise servers.
React and Next.js power a significant portion of modern web applications. Recent market data shows:
A quick search through Shodan this morning, reveals that there are currently around 3800 sites and businesses use a component of React in their web application services. I am unsure how many of these are running the vulnerable version, but we should assume that 10% of these if not more are impacted and vulnerable.
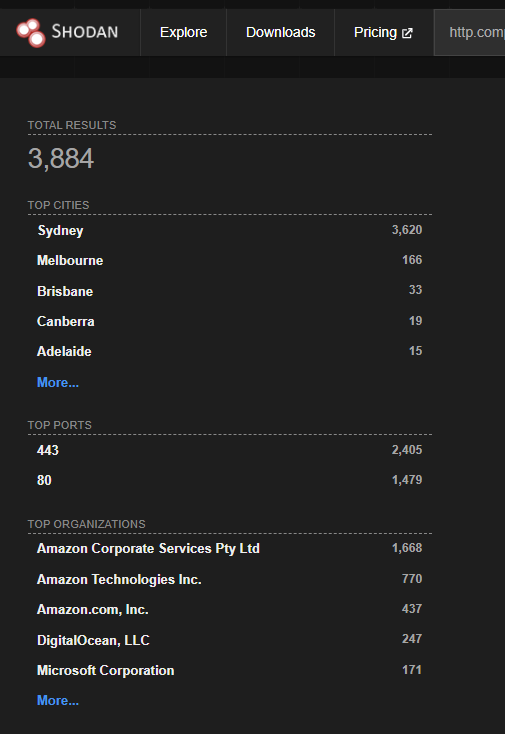
Australian businesses using these libraries and plugins are at high risk if they haven’t patched their systems.
Here where it gets more complicated, running a SaaS/PaaS environment does not mean you are safe and may complicate the situation. You are effectively relying on your vendors to do their job; and while in most the cases, large application vendors do, smaller providers may not effectively monitor or patch their application effectively.
This issue underscores the the hidden cost of software supply chain vulnerabilities. Modern applications depend on hundreds of third-party libraries and frameworks. A single compromised component can impact thousands of customers, akin to the infamous Log4Shell. OWASP’s 2025 Top 10 now lists Software Supply Chain Failures as a critical risk category, highlighting the need for continuous monitoring and secure dependency management.