You’ve trained your users.
You’ve enabled MFA.
You’ve rolled out some email filtering.
And yet…
Somehow, someone still clicked that link.
Now you're chasing a compromised account through logs, praying it hasn’t pivoted into the finance team or domain admins.
Sounds familiar?
That’s because phishing attacks have evolved — and the old playbook doesn’t cut it anymore. This post is your blueprint to secure your org against modern phishing threats, from dodgy QR codes and fake login pages to OAuth abuse and session hijacks.
In this blog I’ll walk you through the stages to tackle this problem.
Let’s stop phishing before it becomes your next cybersecurity nightmare.
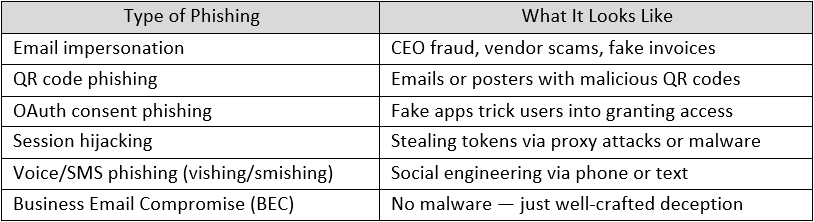
Phishing isn’t just about “bad emails” anymore. It’s now a broad category of social engineering attacks that exploit trust, urgency, and weak access controls — regardless of the delivery method.
We’ve all seen it before.
• “Your invoice is ready – click here to view.”
• “Please sign this document via DocuSign.”
• “Unusual sign-in activity – verify now.”
Here’s what organisations are facing today:
Example :
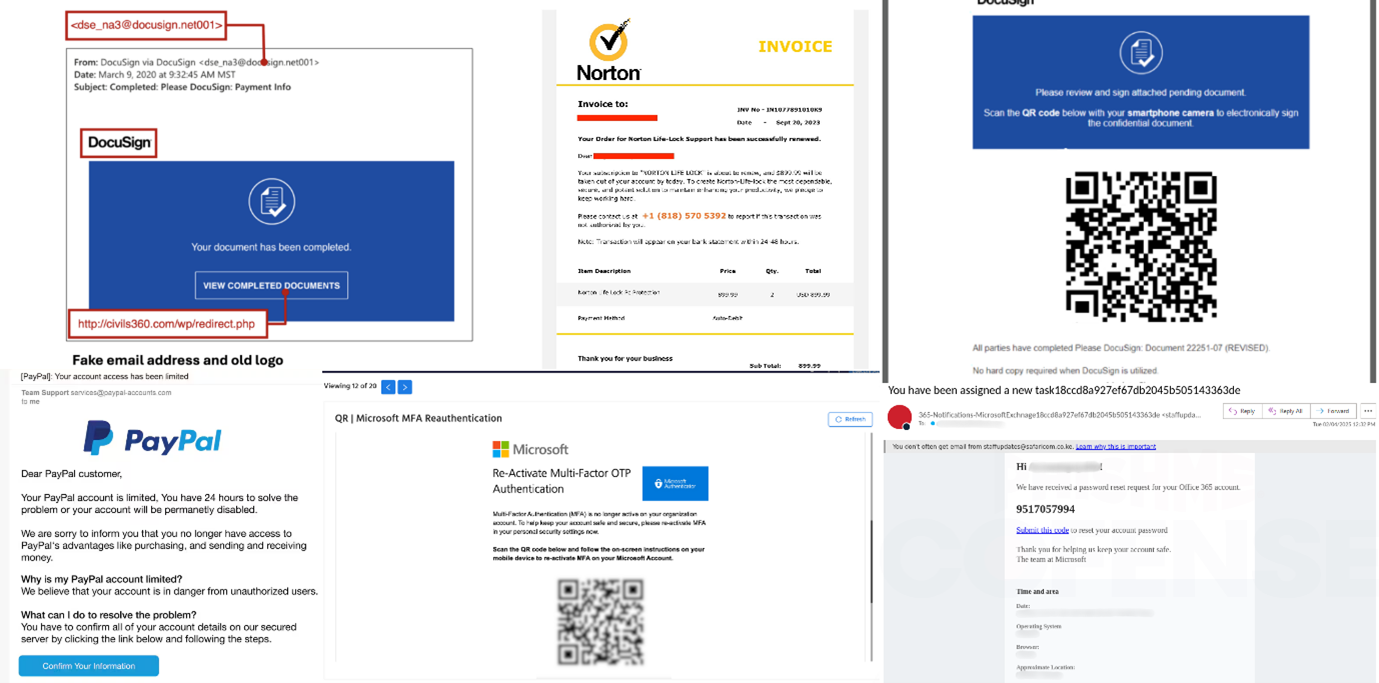
Even with “MFA on everything,” we see attackers phishing the MFA itself (man-in-the-middle attacks), or bypassing it via OAuth. Email filters can’t catch all of this. That’s why identity, device, and context-based controls are your next line of defence.
The goal, then, is to stop the attacker before they can phish credentials or tokens or, failing that, detect and contain immediately when they do.
The evolution: Prevent → Detect → Respond → Harden → Evolve — culminating in phishing-resilient Zero Trust architecture. As their basic principal says, “Verify Explicitly”, “Use Least Privilege Access” and “Assume Breach”
Below is a maturity ladder. Each rung build on the ones below; you’ll want to ensure you have the earlier controls solid before pushing to later stages.

Before you get started, your “house” must be in order, so let’s strengthen the foundations. The first line of defend will be the email security.
Use advanced anti-phishing / anti-impersonation policies through Defender for Office
• Enforce Safe Links, Safe Attachments, real-time click-time scanning
• Enable Zero-Hour Auto Purge — retroactively remove malicious messages
• Use anti-spoof / anti-impersonation policies, lookalike domain detection, and protected users lists
• Use Auto Investigation & Response (AIR) to contain threats from the user inbox
• Add external email banners/flags to visually warn users
• Tune policies carefully (false positives are the enemy) and Spartans can help you in tuning them.
• Allow users to report suspicious emails (e.g. “Report Phishing” button) and feed that back into your policy tuning
• Run regular phishing simulations to test resilience and highlight weak users
Well, every organisation who is aware of security does that, but still gets attacked. If you want Spartans can help you out in configuring defender for office in its best practice.
You don’t want blanket access, you want contextual decisioning. Conditional Access should evaluate multiple signals and require mitigations when risk is high.
Example CA rules you should define:
• Impossible travel / multiple geos: block or require extra challenge (MFA or reauthentication) if sign-ins from disparate locations happen too close in time.
• Geo blocking: Unfamiliar location / risky country: force step-up controls or block entirely.
• Sign-in risk: leverage identity platform’s risk scoring to block or challenge risky sign-ins.
• Device compliance / managed device: require the device be Intune‑enrolled, compliant, or hybrid-joined.
• Session controls / continuous access evaluation (CAE): limit session time, force reauthentication, block downloads, restrict persistent cookies.
• Auth context / step-up MFA triggers: for high‑risk operations (admin portals, payment systems, privileged apps), require reauthentication under stricter policies.
In short: not all logins are equal, your CA policies should dynamically treat them differently. Spartans help organizations to configure the conditional access policy to its best practise.
Even with strong CA rules, if your MFA method can be phished (e.g. push approval, SMS/Call OTP, Software tokens), you have a weak link. You need methods that cannot be captured or replayed in man-in-the-middle.
What counts as phishing-resistant?
Microsoft defines Phishing‑Resistant MFA under its Secure Future Initiative (SFI): methods that prevent AITM or replay attacks — e.g. FIDO2 security keys, passkeys, Windows Hello for Business with platform credentials, certificate-based MFA.
Tip: Start with your high-risk or high-privilege users, test passkey / key deployments, then gradually expand. Spartans offers a rollout guide for phishing-resistant passwordless deployment.
How this looks in practice:
• Enable FIDO2 / passkey / certificate auth in your Authentication Methods policy.
• Create CA policies (in Report-Only mode first) that Require Authentication Strength → Phishing‑Resistant MFA for target user groups.
• Gradually enforce those policies, migrating users off weaker MFA.
• For accounts with privileged roles, Microsoft recommends requiring phishing-resistant MFA.
• Use Temporary Access Pass (TAP) to bootstrap users into phishing-resistant credentials.
If you’d like a plug‑and-play deployment plan for passkeys or build your CA policy roadmap, Spartan Security can help you tailor it exactly to your environment.

Ah, now we're getting into the “worst-case scenario” territory, where you've ticked all the boxes SPF, DKIM, DMARC? Sorted. Defender's running, Safe Links are cracking down, MFA’s on everything that moves,
But what if someone still falls for it?
And worse, they used supply chain to target admins and got successful, then what
At this point, it’s not about stopping the phishing email. It's about limiting what happens next before it compromises the business.
Entra Global Secure Access (GSA) is designed exactly for this moment. when prevention has done its job, but something still slips through. It brings control to what a user can access after authentication, and through which network, device, location and that’s the critical piece most organisations overlook.

Let’s say the compromised account belongs to an admin. Without GSA, that identity could still hit internal apps directly, access sensitive data, or worse — move laterally across your hybrid environment. But with GSA in place, access is dynamically evaluated per session, per app, and per risk level. Just having valid credentials isn’t enough anymore.
Instead of flat, binary access, GSA gives you segmentation at the application layer. Admins can access only what they need, from compliant devices, under safe conditions. If anything looks off like risky sign-in, unmanaged device, non-corporate IP, poor network compliance then GSA can step in to block or isolate the session in real time.
It effectively wraps all access to internal apps, cloud platforms, and even internet browsing in the same Zero Trust control plane. So even if your worst-case phishing scenario plays out, the blast radius is contained.
So, while phishing is still inevitable, compromise doesn’t have to be.
Because GSA is part of Microsoft Entra, it’s backed by the full strength of Microsoft’s identity and security stack. It leverages real-time signals from Microsoft Defender for Endpoint, Identity Protection, and Conditional Access policies. So, if a user signs in from an unusual location, or their device is showing signs of compromise, their access can be blocked or challenged auto, like a risky sign-in, an unmanaged device, a non-corporate IP, or poor network compliance,matically, and instantly.
For businesses, this level of resilience is no longer optional. Whether you’re a startup in Brisbane, a school in Perth, or part of critical infrastructure in Sydney, phishing doesn’t discriminate. But what separates those who bounce back from those who go down hard is how prepared they are after the breach.
Spartans help your organisation in setting up Entra GSA in their best practice for your organisation to stay ahead of these threats.
Because even the best controls sometimes miss something
Just when we thought we’d covered all the bases, we got a wake-up call. One of our helpdesk users received a strange OAuth consent prompt via email. The attacker hadn’t sent a malicious link — instead, they tricked the user into granting access to their mailbox via a rogue app.
This bypassed every traditional phishing control we had. There was no malware, no attachment, and no credential stealing — just a user clicking “Accept.”
We caught it, but it taught us something crucial: You can’t block everything. You need to detect the stuff that gets through.
So, we stepped into the Proactive Detection & Hunting stage.
This isn’t about waiting for alerts, it’s about finding things that look out of place, then responding before they turn into breaches. We integrated Microsoft Defender XDR, Microsoft Sentinel, Defender for cloud apps and Entra Identity Protection, giving us a central place to see risky sign-ins, anomalous permissions, OAuth consents, and strange behaviours.
Spartans helps you out with custom advanced threat hunting queries and detection policies to stay ahead of a full-fledged breach.
Phishing evolves. So must we.
The final stage isn’t about a tool — it’s about a mindset.
We’d spent months deploying tools, tuning policies, and training users. But phishing is like a moving target. Attackers are smart, they test what works, find the gaps, and adjust faster than we think. So, we knew we had to bake continuous improvement into our process.
Here’s what we started doing regularly:
• Risk Assessment: Finding the gaps present in the current environment and plan to take actions against them.
• Compliance Assessment: Benchmarks are already given by the governing bodies to make a baseline for tackling these attacks and safeguard the organisations.
• Quarterly reviews: Reviewing what worked, what backfired, what should be updated and current threats that might target the organisation
• User feedback sessions: Which alerts caused friction? Did they ignore MFA prompts because of too many false positives.
• Simulated phishing: but now targeted, role-based, and scenario-specific (e.g. finance scams during EOFY)
• Red and purple team testing: Internal testing of attack paths, not just perimeter breaches
• Metrics tracking: how many risky sign-ins, blocked attempts, or user-reported phishing emails improved over time and other threat metrics.
One of the biggest wins came from user behaviour. By involving users in security trainings, showing them how their reports helped us catch a real attempt. They became part of the defence. Where the reported phishing numbers went up, actual compromises went down.
Spartans approach is always adaptive, we evolve with current threats to help and protect organisations by providing services like risk assessment, compliance assessment and more.
At the end of the day, phishing is no longer just about someone clicking a dodgy link. It has evolved. Attackers go after your supply chain, exploit OAuth consents, hijack sessions, and lurk quietly behind stolen tokens. And even with all the basics in place i.e., DMARC, Defender, MFA and one clever trick can still slip through. That’s why security can’t stop at prevention. It must continue after the click, when a phish turns into a foothold. That’s where Zero Trust earns its stripes. It doesn’t rely on perfect users or perfect tools. It assumes breach, validates everything, and contains the damage before it becomes a headline.
Start making your organization a secure place with Zero Trust. Don’t treat Zero Trust as “set and forget.” Schedule reviews, perform risk assessments, run fresh phishing campaigns, analyse results, Improve continuously. By the time we reached the end of this Zero Trust journey, our mindset had completely shifted.
At Spartans Security, that’s how we operate, not just by throwing tools at all the problems, but by helping organisations build layered, identity-aware defences that work together. From baseline hardening to adaptive response, we guide teams through the Zero Trust Maturity Model step-by-step, tailored to real-world environments. Because in the modern threat landscape, you can’t fight fire with hope. You fight it with architecture.
Want to see how Spartans Security can help you build Zero Trust that actually works?
Let’s chat. We’ll help you assess where you are, map where you need to go, and back you every step of the way.