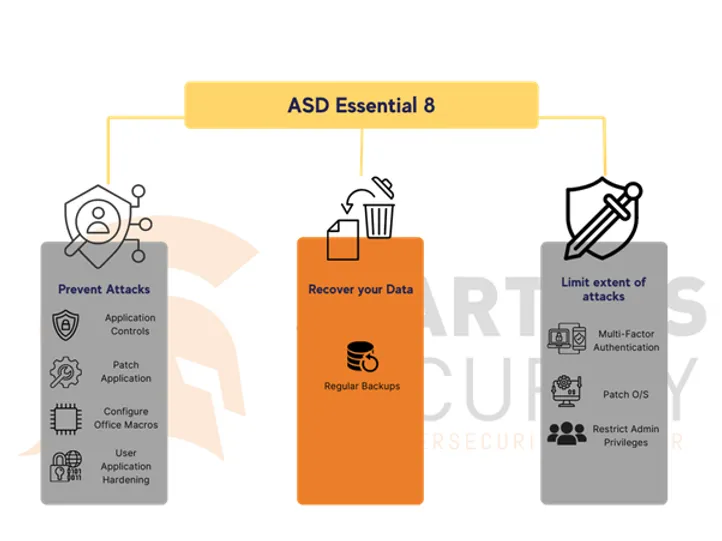
The Australian Signals Directorate (ASD) and Australian Cyber Security Centre (ACSC) recommend that organisations implement eight essential mitigation strategies from the Strategies to Mitigate Cyber Security Incidents as a baseline to protect themselves against various cyber threats. These prioritised mitigation strategies are rated based on their relative security effectiveness from ‘Limited’ to ‘Essential’ and the most effective of these mitigation strategies form the Essential Eight. Implementing the Essential 8, makes it much harder for adversaries to compromise systems, although consider the limitation of Essential 8 as noted in the sections below.
In November 2023, a major update to the ASD/ACSC Essential 8 Maturity Model ushered in significant changes, impacting organisations relying on the framework to guide their information security programs. In this comprehensive guide, we will delve into key modifications, offering insights into how entities can navigate these updates effectively.
Note: The E8 Maturity Model enables organisations to identify and plan for a target maturity level suitable for their environment. Organisations should then progressively implement each maturity level until that target is achieved. Maturity Levels start at zero and progress through to Maturity Level Three.
One of the pivotal changes involves a more robust approach to patching applications and operating systems, particularly those interacting with untrusted internet content.
Organisations are now required to adhere to shorter timeframes for addressing critical vulnerabilities, emphasising the need for a proactive stance on security. The key changes are as follows:
We should note that while Multi-Factor Authentication is an excellent control, not all MFA is created equal. Some MFA methods are prone to attacks such as SMS due to the increase in SIM fraud.
The update introduces stronger requirements for MFA, including new minimum standards at lower maturity levels. Notably, organisations must now implement MFA for user workstations, with specific standards for both internal users and external parties accessing sensitive information portals.
Additionally, emphasis has been placed on adopting so called phishing-resistant MFA methods, ensuring a higher level of security against evolving cyber threats. This involves incorporating further layers of security, such as biometric features or hardware keys, to fortify user authentication. Understanding the nuances of phishing-resistant MFA is critical for organisations seeking to bolster their defences against evolving cyber threats.
The focus on ongoing management and hardening of administrative privileges, application control, and user application hardening is heightened. New governance processes, annual reviews, and specific requirements for securing software environments and script usage have been introduced, underscoring the importance of an holistic security approach.
Implementing Microsoft’s recommended application blocklist and performing annual reviews of application control rulesets is now defined for maturity levels 2 and 3.
The requirement for secure V3 digital signatures for macros at maturity level 3 addresses existing vulnerabilities in macro signature verification that could be exploited in an organisation’s network. Microsoft recommend that after you complete the upgrade to the V3 signatures you enable the “Only trust VBA macros that use V3 signatures” policy setting to make sure that only V3 signature-signed files are trusted. However, logging of macro execution, or the attempt to execute, has been removed. Getting such logging events is a complex process for most organisations.
Disabling or uninstalling Internet Explorer 11 is now a requirement across all maturity levels. Some legacy systems may require IE11, however organisations should be well and truly moving on from needing to use IE11.
Emphasis on hardening systems using the ASD or vendor hardening guides has been added, with the caveat that the most stringent of the two is used. This could present a challenge for most organisations where such hardening processes may restrict the open collaboration required between employees, partners, and clients.
While not much has changed in the realm of backups, organisations are now urged to consider the criticality of the data being backed up. Assessing the Recovery Time Objective (RTO) and Recovery Point Objective (RPO) for each business system is vital to providing evidence of compliance with this mitigation strategy.
Adopting backup technology that provides immutable backup images prevents attackers from corrupting your backup system, which is a common tactic we see during incidents and data breaches.
Finally, we note that regular and comprehensive testing of backup images to ensure that they can be relied on during incidents and/or disasters is critical. This comprehensive testing is often missed and should be built into your backup and disaster recovery regime.
A notable addition is the requirement for centralised event log management - a key component for organisations aiming to achieve and maintain maturity level 2 or higher. Exploring the need for external expertise, such as engaging trusted partners for a Security Information and Event Management (SIEM) or Managed Detection and Response (MDR) solution, becomes essential.
For the first time, organisations are obligated to report cybersecurity incidents to their nominated Chief Information Security Officer (CISO) or equivalent as well as the relevant authorities such as the ACSC and the Office of the Information Commissioner. Developing and maintaining cybersecurity incident response plans is now a prerequisite for maturity level 2 and higher against most mitigation strategies.
It’s important to stress that the Essential 8 are only the “Essential” strategies from a long list that the ASD/ACSC compiles based on current threats and intelligence. They are not sufficient to mitigate all risks and/or attacks and represent basic cyber security hygiene. For a comprehensive approach, consider adopting a more complete set of controls such as the ASD Top 35, Information Security Manual (ISM), NIST CSF and/or ISO 27002 controls or another best practice framework that suits your environment.
As security is an ongoing journey, once businesses progress through the ASD framework implementation, they can consider starting their journey towards Zero Trust.
In addition to Essential 8 and Top 35, organisations need an overarching risk framework that identifies what controls are needed - there are a plethora of risk frameworks that can assist in this effort.
We recommend adopting NIST CSF as an overarching cyber security framework. NIST provides 5 “plain-English” key functions that make this control set suitable for both technologists and business leaders.
The 5 NIST functions, Identify, Protect, Detect, Respond and Recover can be well understood by business, IT, and senior executives.
Our view is that the relationship between Risk Framework (i.e. NIST) and Control Framework (i.e. Essential 8) can be demonstrated in the diagram below. Additionally, both should be underpinned by a strong security governance foundation (i.e. the bottom of the pyramid below)

Spartans Security can play a valuable role in helping assess compliance against the Essential 8 Maturity Model and providing a roadmap to uplift cyber resilience that addresses various aspects of the threat landscape. Additionally, our team can assist organisations in building a security program aligned with industry best practices and ensure ongoing improvements and risk-based decision making.
Spartans Security's expert team can help organisations to create a formidable shield against the most prevalent cyber threats by adopting proper cybersecurity standards and best practices.
For more detailed information on the changes to the Essential 8 Maturity Model, entities are encouraged to visit the official ASD/ACSC website at https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight/essential-eight-maturity-model-changes.
There’s a lot to unpack here! Fundamentally, the changes represent more work for organisations that are using the Essential 8 Maturity Model as their information security framework, especially those that want to hit maturity level 2 or higher.
The recent Essential 8 Maturity Model updates bring forth a paradigm shift in the way organisations approach information security. While these changes may represent an increased workload, understanding and adapting to them is crucial for maintaining compliance and ensuring a robust cybersecurity posture. So don’t let these changes put you off of jumping into your own Essential 8 journey as help is always at hand.
If you have any questions, get in touch at info@spartanssec.com