
Let’s not sugarcoat it. If you're walking out of yet another board meeting or a management meeting empty-handed, without that much-needed bump in your cybersecurity budget, it’s time to go back to the drawing board. In my experience working with dozens of CIOs, CISOs, and cyber leads across various industries, one painful truth keeps surfacing: you didn’t get the budget because you didn’t bring the right story to the table. You brought fear, uncertainty, and doubt. What you needed to bring were numbers, context, and proof.
In my experience, Boards don’t hate cybersecurity. They just need clarity. Many CIOs and CISOs often walk into these meetings waving irrelevant, vague charts, talking about ransomware, nation-state actors, or vulnerabilities without any grounding in the organisation’s actual operations.
What’s missing? Hard data. Not just anecdotes or general industry scare tactics. You didn’t explain what’s specifically at risk in your business. You didn’t show how their current investment in cyber is performing. You couldn’t measure impact. You didn’t quantify risk. You couldn’t articulate return on investment or loss expectancy. These are the strong reasons why the board said no.
Are you measuring the efficiency of the committed resources and the efficacy of the controls you have invested in?
Let me ask you this: When’s the last time you looked at your organisation’s KPI (Key Performance Indicators) for cybersecurity? Or your KCI (Key Control Indicators)? Or even your KRI (Key Risk Indicators)? If you're not using a structured measurement framework, you’re flying blind. Worse, you're expecting the board to fund your flight. The result? They deprioritise the cyber budget.
It’s about tracking specific controls and outcomes over time. For example:
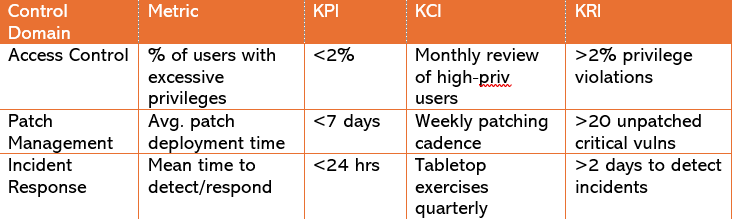
With something like this, you’re not just saying “We need more money because attacks are increasing.” You’re showing that your detection times are 48 hours, and with the right investment, you can cut it to 8. That’s real data, related data and business value data.
Here’s what frustrates me the most: even senior IT and cyber execs are not actively monitoring their day-to-day activities in a meaningful way. They’re doing the work, but they rarely measure controls in a way that provides real data.
If you’re too busy to measure, you’re too busy to manage. You don’t need a certificate course in cybersecurity metrics to determine if your controls are effective. But you do need a baseline, and you do need visibility.
Let me give you a few practical examples:
• Firewall Rule Review: Instead of saying “Our firewalls are well-configured,” measure how many rules are outdated, how often reviews are conducted, and whether they align with your threat model.
• User Awareness Training: Don’t just tell the board, “We conduct security training.” Tell them, “Only 4% of staff failed the last phishing simulation—down from 12% last quarter.”
• Third-Party Risk: Track the percentage of third parties who have completed risk assessments or have valid security certifications like ISO/IEC27001 and SOC 2 Type II. That’s a KCI.
• Endpoint Protection: Measure how many endpoints are unprotected at any given time. That’s your exposure. That’s your KRI.
This isn’t just checkbox compliance. This is how you show business-aligned cybersecurity that brings clarity and speaks the language the management understands.
These monitoring and measurements aren’t just ticking compliance boxes. It’s giving you a dynamic dashboard to communicate cybersecurity value in business terms:
• KPIs show how well your security performs.
• KCIs demonstrate that your controls are functioning correctly.
• KRIs flag where your risk is creeping up—fast.
Pro Tip: When you walk into your next board meeting, don’t just show this table. Translate it into a simple traffic-light scorecard: Green, Yellow, and Red. Tie each red to a budget task. Now you're not just asking for money, you are presenting risks.
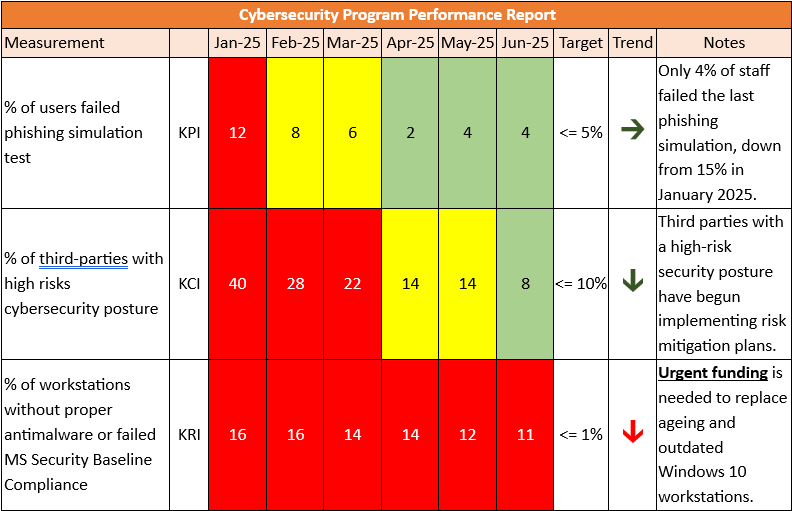
Most CISOs I meet talk a big game about risk, but when you peel back the layers, they don’t track it. They don’t monitor whether their controls are working the way they should. They aren’t measuring impact. That’s where KPI, KCI, and KRI become your essential trinity for monitoring your performance, return on investment and time spent by your team.
• KPI (Key Performance Indicator): Are your processes efficient? Are you patching quickly? Are incidents being contained in time?
• KCI (Key Control Indicator): Are the controls in place, and are they doing what they’re supposed to? Is your firewall being reviewed? Is user access being checked?
• KRI (Key Risk Indicator): What’s the risk that something bad will happen soon? Are too many endpoints unprotected? Are you seeing too many phishing test failures?
Once you start monitoring and measuring using this framework, your conversations with the board shift from “trust me, I need more budget” to “here’s the risk, here’s the performance, and here’s the cost to fix it.”
Most boards don’t care about cyber because we haven’t done a good job connecting it to business outcomes. Don’t be stuck in IT jargon, such as CVEs and MITRE ATT&CK.
Here's how you shift the narrative:
• Instead of: “We need a new SIEM platform.”
• Say: “We need a platform that reduces our incident detection time by 80%, cutting down risk exposure windows and minimising downtime.”
• Instead of: “We’re exposed to ransomware.”
• Say: “Right now, our backups are failing on 5% of critical systems. A ransomware or system failure would cost us X. A fix costs Y.”
Make it about risk reduction, revenue protection, and customer trust.
The Board needs to feel you are not managing cyber by gut feel.
The Bottom Line: Visibility Builds Credibility
Boards don’t want technical jargon. They want assurance. They want to know:
• What’s at risk?
• What are you doing about it?
• Is it working?
• What does it cost to improve?
Metrics give you that assurance. They also provide you with credibility. When you walk into the boardroom with a crisp dashboard showing where you stand, where you’re headed, and what you need to get there, you shift from cost centre to strategic advisor.
If you’ve been struggling to secure that cyber budget boost, it’s not because the board doesn’t care. It’s because you didn’t give them a reason to care. You didn’t show them the metrics. You didn’t show them the risk. And you didn’t tie your ask to the business’s bottom line. Spartans Security helps organisations manage and monitor their cybersecurity programs through expert assessments and the development of a tailored monitoring matrix, enabling you to understand how your investment and cyber program are performing and create a foundation for clarity.
You want to discuss this further, contact us at Spartans Security.